Understanding Zero Trust: A Comprehensive Overview
Introduction to Zero Trust
Zero Trust is a security framework designed to protect organizations by requiring rigorous authentication and continuous validation of users and devices before granting or maintaining access to applications and data. Unlike traditional security models that operate on the assumption that everything inside the network perimeter is trustworthy, Zero Trust operates on the principle that no user or device should be implicitly trusted. This framework is crucial for managing modern security challenges, including remote work, hybrid cloud environments, and advanced threats like ransomware.
Key Principles of Zero Trust
- Continuous Verification: Always validate user identities, device health, and the security posture continuously rather than relying on a one-time verification.
- Limit the Blast Radius: Minimize the potential damage of breaches by limiting the extent of access for users and devices, thereby reducing the scope of an attack.
- Automate Context Collection and Response: Use automated systems to gather contextual information from various IT components (identity, endpoint, workload) and respond to threats in real time.
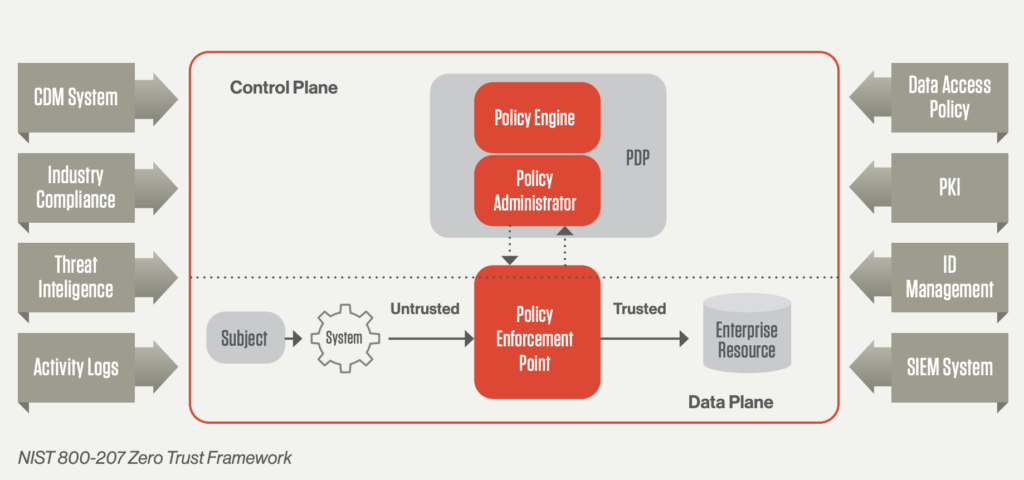
Zero Trust and NIST 800-207
The NIST 800-207 standard provides a comprehensive and vendor-neutral approach to implementing Zero Trust. It aligns with other frameworks like Forrester’s ZTX and Gartner’s CARTA, focusing on ensuring compatibility and protection against modern cyber threats. In response to a surge in high-profile security breaches, the Biden administration mandated U.S. Federal Agencies to adhere to NIST 800-207, validating its relevance and applicability to both public and private sectors.
How Zero Trust Works
Zero Trust architecture requires continuous assessment of users, devices, and their interactions with the network. This involves:
- Advanced Technologies: Implementing risk-based multi-factor authentication, next-generation endpoint security, and robust cloud workload technologies.
- Encryption and Data Protection: Ensuring data security through encryption and securing email and other communication channels.
- Continuous Monitoring: Regularly validating user credentials and device integrity to prevent unauthorized access.
The Evolution from Traditional Security Models
Traditional security models operated on a “trust but verify” basis, where users and devices inside the network perimeter were considered trustworthy by default. This approach proved inadequate in the face of cloud migration and the rise of remote work, exposing organizations to risks from both internal and external threats. Zero Trust addresses these limitations by enforcing stringent verification and continuous monitoring, thus providing robust protection against sophisticated attacks.
Zero Trust Implementation Steps
- Define Objectives: Align Zero Trust goals with overall business strategies.
- Identify Value Streams: Analyze and map critical processes and data flows within the organization.
- Design and Implement: Develop a Zero Trust architecture tailored to organizational needs, incorporating necessary technologies and policies.
- Monitor and Optimize: Continuously evaluate the effectiveness of the Zero Trust framework and make adjustments based on performance metrics and evolving threats.
Overcoming Implementation Challenges
- Resistance to Change: Engage employees by communicating the benefits and providing adequate training.
- Cultural Shifts: Foster a culture of continuous improvement and security awareness.
- Leadership Commitment: Ensure senior management is actively involved and supportive of Zero Trust initiatives.
Measuring Success
Key performance indicators (KPIs) to measure the effectiveness of Zero Trust include:
- Access Control Effectiveness: Evaluate how well the framework manages and restricts access.
- Incident Response Time: Measure the speed and efficiency of detecting and responding to security incidents.
- User Experience: Assess how Zero Trust impacts the user experience, ensuring it does not hinder productivity.
Zero Trust Use Cases
Zero Trust is beneficial for organizations with:
- Complex Infrastructure: Multi-cloud, hybrid environments, and unmanaged devices.
- High Threat Environments: Organizations facing significant ransomware, supply chain attacks, or insider threats.
- Compliance Requirements: Industries with strict regulatory and compliance needs.
Example: The Sunburst Attack
The 2021 Sunburst attack underscored the necessity of Zero Trust principles. By exploiting a trusted tool and leveraging an over-permissioned service account, attackers were able to move laterally within the network. Zero Trust would have limited the impact by enforcing strict access controls and continuous monitoring of service accounts.
Why Choose CrowdStrike for Zero Trust?
CrowdStrike offers a frictionless approach to Zero Trust, adhering to NIST 800-207 standards and providing:
- Comprehensive Protection: Coverage for endpoints, cloud workloads, and data.
- Advanced Detection and Response: Hyper-accurate threat detection and automated protection.
- Reduced Complexity and Costs: Simplified deployment and management through the CrowdStrike Security Cloud.
Conclusion
Zero Trust is a critical framework for modern cybersecurity, addressing the complexities of today’s digital landscape. By adopting Zero Trust principles, organizations can enhance their security posture, reduce the impact of breaches, and align with industry standards and regulations. For a more detailed exploration of Zero Trust implementation and best practices, consult the relevant standards and consider leveraging solutions like CrowdStrike for effective deployment.
Feel free to adjust or add any specific details relevant to your context!